

Become a Certified Cybersecurity Technician (C|CT)
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






EC-Council has developed the Certified Cybersecurity Technician certification
The Certified Cybersecurity Technician (C|CT) is an entry-level cybersecurity program created by EC-Council, the creator of the Certified Ethical Hacker (C|EH) certification, to address the global demand for a qualified cybersecurity workforce.
EC-Council developed the C|CT to provide individuals starting their careers in IT and cybersecurity with a certification that validates their hands-on technical skills.
To equip individuals with the skills they need to pursue and develop their careers as cybersecurity specialists, consultants, network engineers, IT administrators, and more.
What is Unique About the C|CT Program?
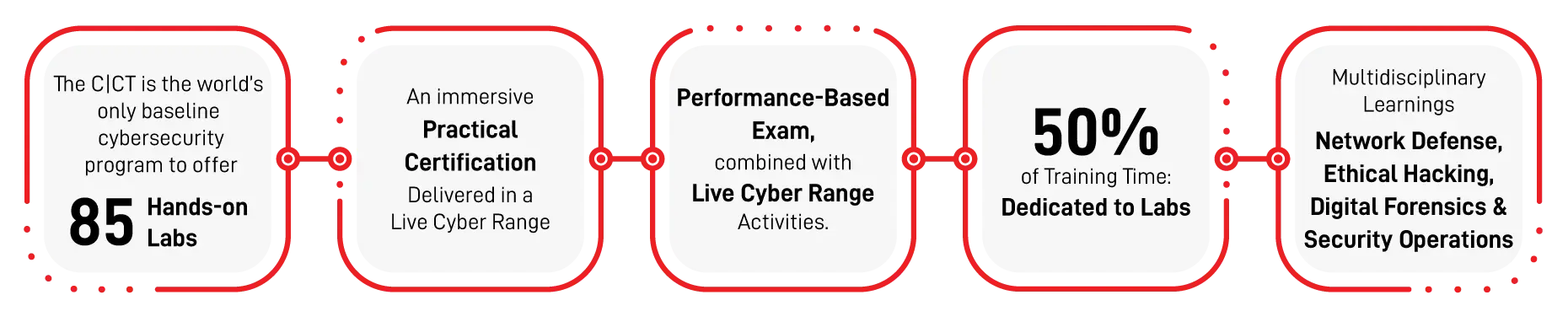
C|CT’s Key Offerings:
Strong Foundational Coverage
The C|CT certification provides total foundational cybersecurity domain coverage with key concepts in each domain combined with practical hands-on labs and critical thinking challenges producing world-class cyber security technologists.
The C|CT certification provides total foundational cybersecurity domain coverage with key concepts in each domain combined with practical hands-on labs and critical thinking challenges producing world-class cyber security technologists.
Live Range Experience
Other popular programs rely on simulation and interactivity as practical-based assessment, the C|CT program is delivered on a live Cyber Range utilizing live targets and real attack systems for a truly immersive, real-life practice and assessment platform.
Other popular programs rely on simulation and interactivity as practical-based assessment, the C|CT program is delivered on a live Cyber Range utilizing live targets and real attack systems for a truly immersive, real-life practice and assessment platform.
Capture the Flag
The C|CT certification offers capture the flag (CTF) style critical thinking challenges to accompany each lab exercise putting knowledge into practice and providing a proven record of skill demonstration. Candidates completing the C|CT program will earn the C|CT certification and have a proven track record of performing the tasks required in a live Cyber Range, proving to employers their ability to perform critical job duties.
The C|CT certification offers capture the flag (CTF) style critical thinking challenges to accompany each lab exercise putting knowledge into practice and providing a proven record of skill demonstration. Candidates completing the C|CT program will earn the C|CT certification and have a proven track record of performing the tasks required in a live Cyber Range, proving to employers their ability to perform critical job duties.
Multiple Certifications
The course outline of the C|CT program goes above and beyond some of the more common entry-level cybersecurity programs, such as the Security+, in a completely hands-on cyber range environment instead of simulations to ensure cybersecurity skills development. We believe that candidates who successfully attain the C|CT certification will attain other leading cybersecurity certifications, including Security+, without further training
The course outline of the C|CT program goes above and beyond some of the more common entry-level cybersecurity programs, such as the Security+, in a completely hands-on cyber range environment instead of simulations to ensure cybersecurity skills development. We believe that candidates who successfully attain the C|CT certification will attain other leading cybersecurity certifications, including Security+, without further training
Most Affordable
Despite the unique design of the heavily hands-on course and its uses of real-world cyber range capability, the certification is one of the most affordable in the world!
Despite the unique design of the heavily hands-on course and its uses of real-world cyber range capability, the certification is one of the most affordable in the world!
What Are the Benefits of the C|CT Credential?
Paves the way for a promising career in the realm of cybersecurityTeaches the fundamental knowledge that cybersecurity professionals need:
-
- Information security
- Network security
- Computer forensics
- Risk management
- Incident handling
- Industry best practices
Provides extensive opportunities to practice the hands-on skills necessary for any technical role involving administrative privileges and cybersecurity considerations
Enroll now to get details on Plans & Pricing

Program Information
- Course Module
- What will you learn?
- Training Options
- About the Exam
Course Module
| Module 01: Information Security Threats and Vulnerabilities |
| Module 02: Information Security Attacks |
| Module 03: Network Security Fundamentals |
| Module 04: Identification, Authentication, and Authorization |
| Module 05: Network Security Controls – Administrative Controls |
| Module 06: Network Security Controls – Physical Controls |
| Module 07: Network Security Controls – Technical Controls |
| Module 08: Network Security Assessment Techniques and Tools |
| Module 09: Application Security |
| Module 10: Virtualization and Cloud Computing |
| Module 11: Wireless Network Security |
| Module 12: Mobile Device Security |
| Module 13: IoT and OT Security |
| Module 14: Cryptography |
| Module 15: Data Security |
| Module 16: Network Troubleshooting |
| Module 17: Network Traffic Monitoring |
| Module 18: Network Logs Monitoring and Analysis |
| Module 19: Incident Response |
| Module 20: Computer Forensics |
| Module 21: Business Continuity and Disaster Recovery |
| Module 22: Risk Management |
| 1. Key issues plaguing the cybersecurity industry (information security and network security) |
| 2. Information security threats, vulnerabilities, and attacks |
| 3. Different types of malware |
| 4. Network security fundamentals |
| 5. Identification, authentication, and authorization concepts |
6. Network security controls
|
| 7. Network security assessment techniques and tools (threat hunting, threat intelligence, vulnerability assessment, ethical hacking, penetration testing, and configuration and asset management) |
| 8. Application security design and testing techniques |
| 9. Fundamentals of virtualization, cloud computing, and cloud security |
| 10. Wireless network fundamentals, wireless encryption, and security measures |
| 11. Fundamentals of mobile, IoT, and OT devices and their security measures |
| 12. Cryptography and public key infrastructure concepts |
| 13. Data security controls, data backup and retention methods, and data loss prevention techniques |
| 14. Network troubleshooting, traffic monitoring, log monitoring, and analysis for suspicious traffic |
| 15. Incident handling and response process |
| 16. Computer forensics fundaments, digital evidence, and forensic investigation phases |
| Title of the Course: | Certified Cybersecurity Technician (CCT) |
| Training Duration: | 5 Days |
| Delivery Mode: |
|
| Exam Title | Certified Cybersecurity Technician |
| Exam Code | 212-82 |
| Number of Questions | 60 |
| Duration | 3 hours |
| Exam Availability Locations | ECC Exam Portal |
| Languages | English |
| Test Format | Multiple Choice and Real Life hands-on Practical Exam |
| Passing Score | 70% |
| Exam Mode | Remote Proctoring Services |
Enroll now to get details on Plans & Pricing
C|CT – Become a Responsible Cyber Operator in Any IT Role:
The C|CT program allows individuals to eventually grow their skills into various roles, including penetration testing, security consulting, auditor and administrator roles, and beyond. It establishes a foundation of technical skills required to create successful technologists who will advance across various work roles.Job Description of a Cybersecurity Technician:
A professional who provides technical cybersecurity support, troubleshoots network security problems, monitors alerts, and follows policies, procedures, and standards to protect information assets.Job Opportunities & Job Roles for C|CT Credential:
The Certified Cybersecurity Technician certification prepares IT and Cybersecurity professionals for a wide range of complex issues that focus on securing software, networks, and IT systems while understanding common threats and attacks. C|CT offers a multifaceted approach to network defense, ethical hacking, and security operations to ensure individuals use their strongest abilities to configure, analyze, and identify problems within their organization. This course will prepare and enhance skills in the following roles:
IT Support Specialist
IT Networking Specialist
Cybersecurity Technicians
Network Engineers
SOC Analyst
IT Managers
Enroll now to get details on Plans & Pricing
Who Can Attend This Course?
The C|CT course can be taken by students, IT professionals, IT managers, career changers, and any individual seeking a career in cybersecurity, or aspiring to advance their existing role. This course is ideal for those entering the cybersecurity workforce, providing foundational technician level, hands-on skills to solve the most common security issues organizations face today.
Who Can Attend This Course?
The C|CT course can be taken by students, IT professionals, IT managers, career changers, and any individual seeking a career in cybersecurity, or aspiring to advance their existing role. This course is ideal for those entering the cybersecurity workforce, providing foundational technician level, hands-on skills to solve the most common security issues organizations face today.
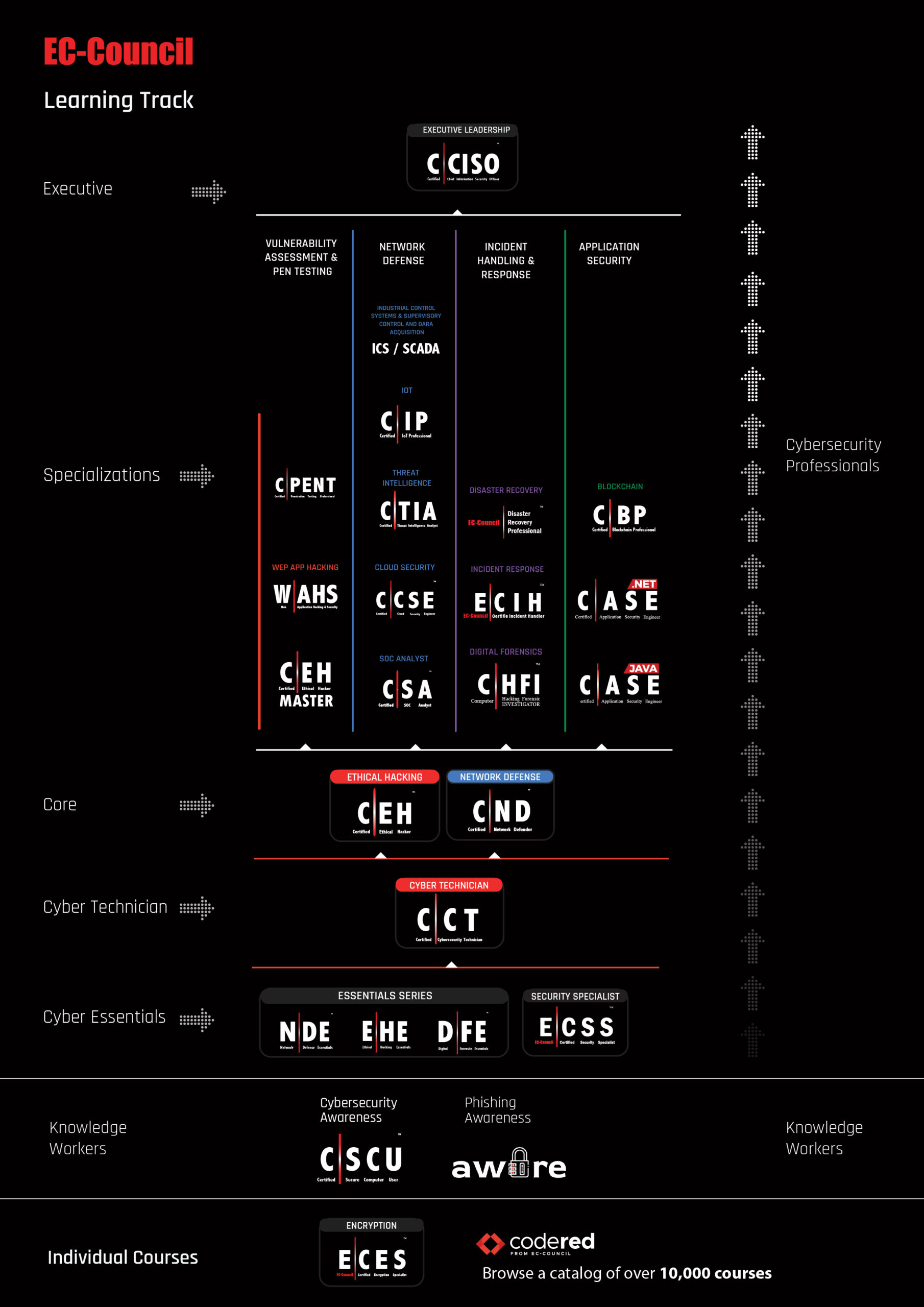
Cybersecurity Career Starter Track:

EC-Council Certification Learning Track:.
Accreditations, Recognitions & Endorsements





